Projects
Side projects I’ve been working on over the past couple of years in somewhat reverse chronological order.
- 2024/04-present Asbury Park happy hours
- Static website listing happy hours in Asbury Park, NJ. Used to be jekyll, rewrote in Rust using minininja. The “database” is a RON file.
- 2026/02 ntsc
- frei0r video filter plugin that uses ntsc.rs to emulate analog TV and VHS artifacts.
- 2026/01-2026/02 cyd-video
- Rust no_std video player for the CYD (“Cheap Yellow Display) ESP32-2432S028R microcontroller. It works but the performance is not good enough. It’s based on MJPEG using the tjpgdec-rs decoder (see below) and riffparse (see below).
- 2026/01-2026/02 riffparse
- Rust no_std RIFF/AVI video format demuxer. Extracts audio amd video frames from an AVI file.
- 2025/05-2026/02 frei0r-rs2
- Fork of the Rust frei0r-rs framework for building frei0r video plugins in Rust. Made major changes to the API.
- 2026/02 tjpgdec-rs
- Some vibe-coded performance improvements to the tjpgdec-rs JPEG decoder used with cyd-video.
- 2026/02 esp32-tv
- ESP32 video player fork with vibe coded fixes and support for IR receiver.
- 2026/01 esp32-202432S028_video_player
- ESP32 video player fork, ported to platformio.
- 2026/01 cyd-bevy-life
- Conway’s game of life on no_std ESP32 MCU...
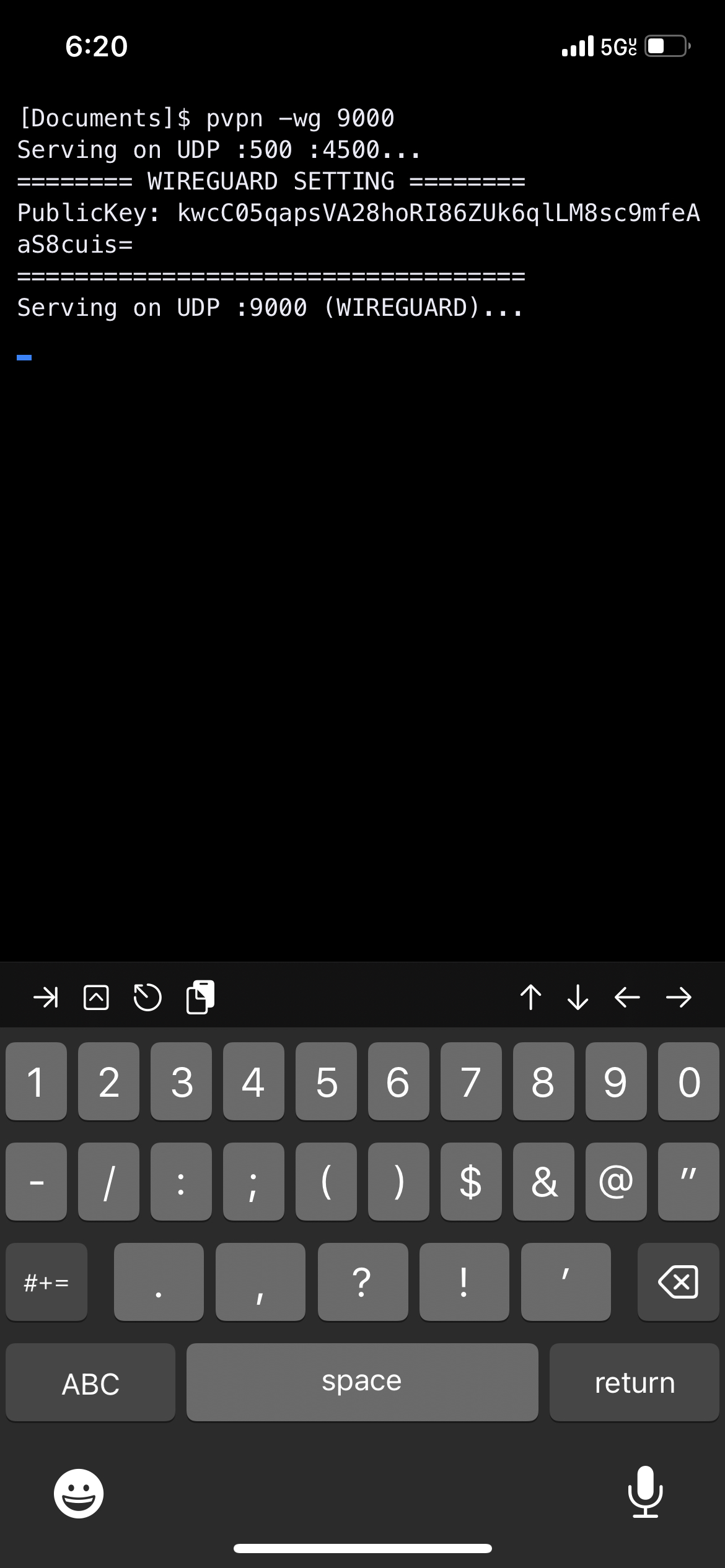 Copy the
Copy the